Entropy | Free Full-Text | On the Security of Offloading Post-Processing for Quantum Key Distribution
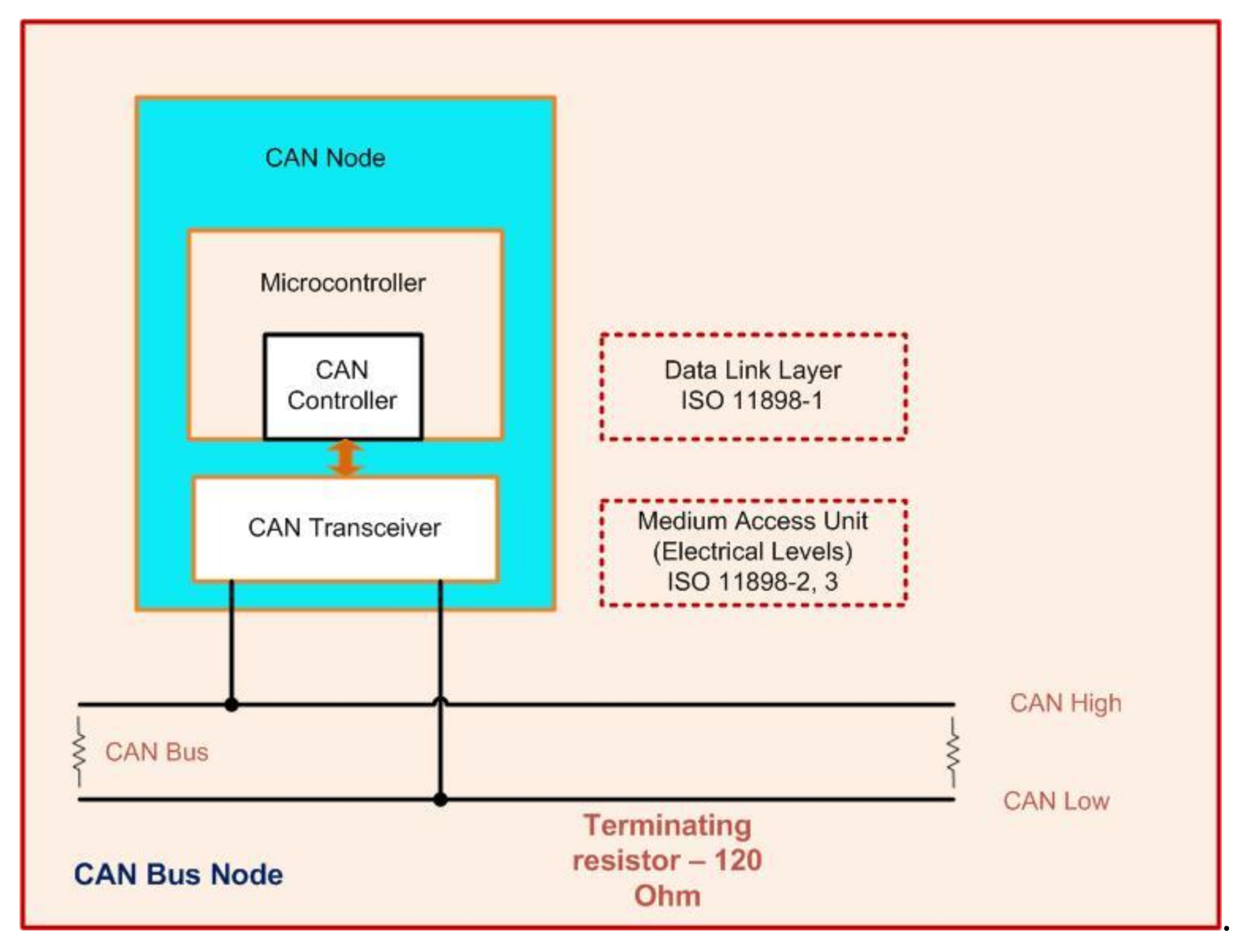
Electronics | Free Full-Text | Security Issues with In-Vehicle Networks, and Enhanced Countermeasures Based on Blockchain
Testing the New Version of the Windows Security Events Connector with Azure Sentinel To-Go! - Microsoft Community Hub
itr verification: Forgot to verify your income tax return? Here is what you can do - The Economic Times
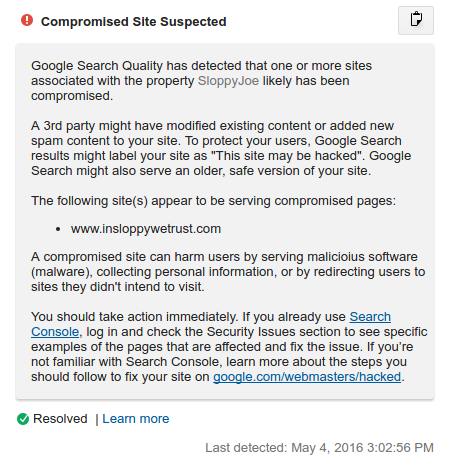
Webmasters - configure Google services at your hosting panel | Google Search Central Blog | Google Developers
GitHub - auth0/node-jsonwebtoken: JsonWebToken implementation for node.js http://self-issued.info/docs/draft-ietf-oauth-json-web-token.html